国内外b2b网站网址有哪些网站google搜索优化
公众号关注 「奇妙的 Linux 世界」
设为「星标」,每天带你玩转 Linux !

Permission Manager 是一个简单便捷的 RBAC 管理界面工具,支持通过 Web 界面创建用户,分配 Namespace 权限,并可以生成相应的 Kubeconfig 文件。
项目地址:https://github.com/sighupio/permission-manager.git
1安装 Permission Manager
下载源代码
$ git clone https://github.com/sighupio/permission-manager.git
正克隆到 'permission-manager'...
remote: Enumerating objects: 2350, done.
remote: Counting objects: 100% (593/593), done.
remote: Compressing objects: 100% (395/395), done.
remote: Total 2350 (delta 388), reused 349 (delta 189), pack-reused 1757
接收对象中: 100% (2350/2350), 10.79 MiB | 3.57 MiB/s, done.
处理 delta 中: 100% (1427/1427), done.
$ cd permission-manager/
$ ls
cmd development Dockerfile e2e-test go.sum internal Makefile reltag.sh tests
deployments development-compose.yml docs go.mod helm_chart LICENSE.md README.md statik web-client
## 部署文件位于 deployments/kubernetes 下
$ ls deployments/kubernetes/
deploy.yml seeds
$ ls deployments/kubernetes/seeds/
crd.yml seed.yml创建 namespace
$ kubectl create namespace permission-manager创建一个存储配置的 Secert
---
apiVersion: v1
kind: Secret
metadata:name: permission-managernamespace: permission-manager
type: Opaque
stringData:PORT: "4000" # port where server is exposedCLUSTER_NAME: "my-cluster" # name of the cluster to use in the generated kubeconfig fileCONTROL_PLANE_ADDRESS: "https://apiserver.cluster.local:6443" # full address of the control plane to use in the generated kubeconfig fileBASIC_AUTH_PASSWORD: "changeMe" # password used by basic auth (username is `admin`)参数解释:
| PORT | 服务端口号 |
|---|---|
| CLUSTER_NAME | 要在生成的 kubeconfig 中使用的集群名称 |
| CONTROL_PLANE_ADDRESS | 在生成的 kubeconfig 文件中使用的控制平面的地址 |
| BASIC_AUTH_PASSWORD | web 页面的登陆密码,默认登录账户为 admin |
通过 YAML 部署 CRD 以及预定义的一些权限
$ kubectl apply -f seeds/
customresourcedefinition.apiextensions.k8s.io/permissionmanagerusers.permissionmanager.user created
clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___operation created
clusterrole.rbac.authorization.k8s.io/template-namespaced-resources___developer created
clusterrole.rbac.authorization.k8s.io/template-cluster-resources___read-only created
clusterrole.rbac.authorization.k8s.io/template-cluster-resources___admin created# 创建了 admin,read-only,developer 三个权限供 web 页面使用
$ kubectl get clusterrole|grep ^template
template-cluster-resources___admin 2021-08-06T02:55:10Z
template-cluster-resources___read-only 2021-08-06T02:55:10Z
template-namespaced-resources___developer 2021-08-06T02:55:10Z
template-namespaced-resources___operation 2021-08-06T02:55:10Z
点击上方图片,打开小程序,『饿了么外卖』红包免费领!
部署 Deployment
$ kubectl apply -f deploy.yml
service/permission-manager created
deployment.apps/permission-manager created
serviceaccount/permission-manager created
clusterrole.rbac.authorization.k8s.io/permission-manager created
clusterrolebinding.rbac.authorization.k8s.io/permission-manager created$ kubectl get pod -n permission-manager
NAME READY STATUS RESTARTS AGE
permission-manager-bdddff74b-4pv67 1/1 Running 0 5m9s创建 Ingerss 文件(Traefik)
$ cat permission-manager-ingress.yaml
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:name: permission-managernamespace: permission-manager
spec:entryPoints:- webroutes:- match: Host(`rbac.lishuai.fun`)kind: Ruleservices:- name: permission-managerport: 4000
---
apiVersion: traefik.containo.us/v1alpha1
kind: IngressRoute
metadata:annotations:prometheus.io/http-probe: "true"name: permission-manager-tlsnamespace: permission-manager
spec:entryPoints:- websecureroutes:- match: Host(`rbac.lishuai.fun`)kind: Ruleservices:- name: permission-managerport: 4000tls:certResolver: myresolver注:创建 Ingerss 资源不是必需的,这里是以 Traefik 为例。你可以根据自身情况变更为 Nginx Ingress 或者直接使用 NodePort 进行服务对外暴露。
2使用 Permission Manager
首次打开 Permission Manager 登陆页面,会让我们输入用户名和密码,用户名为 admin,密码就是上面的 secert.yaml 文件中定义的 BASIC_AUTH_PASSWORD。登陆后,首页如下:
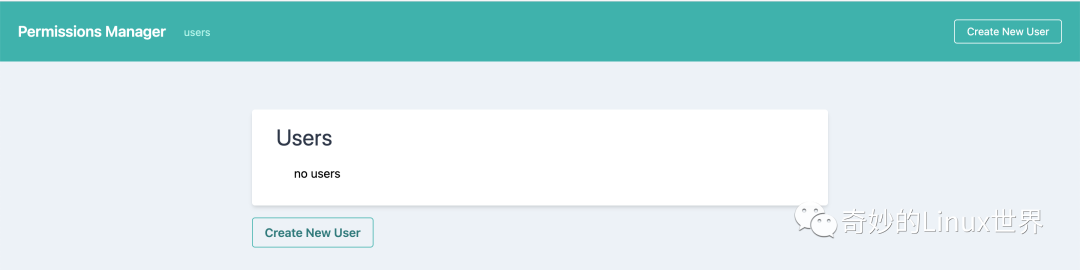
新建用户
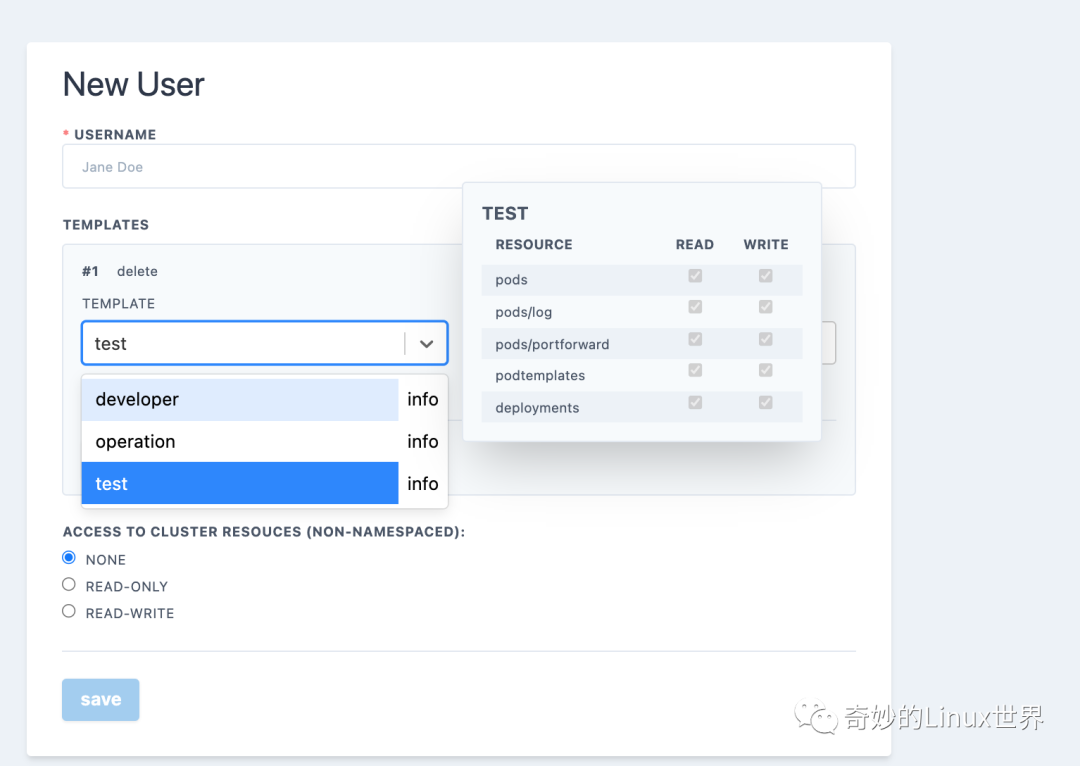
我们点击首页的create new user去创建一个用户授予其拥有访问 monitoring 这个 namespace 的权限。
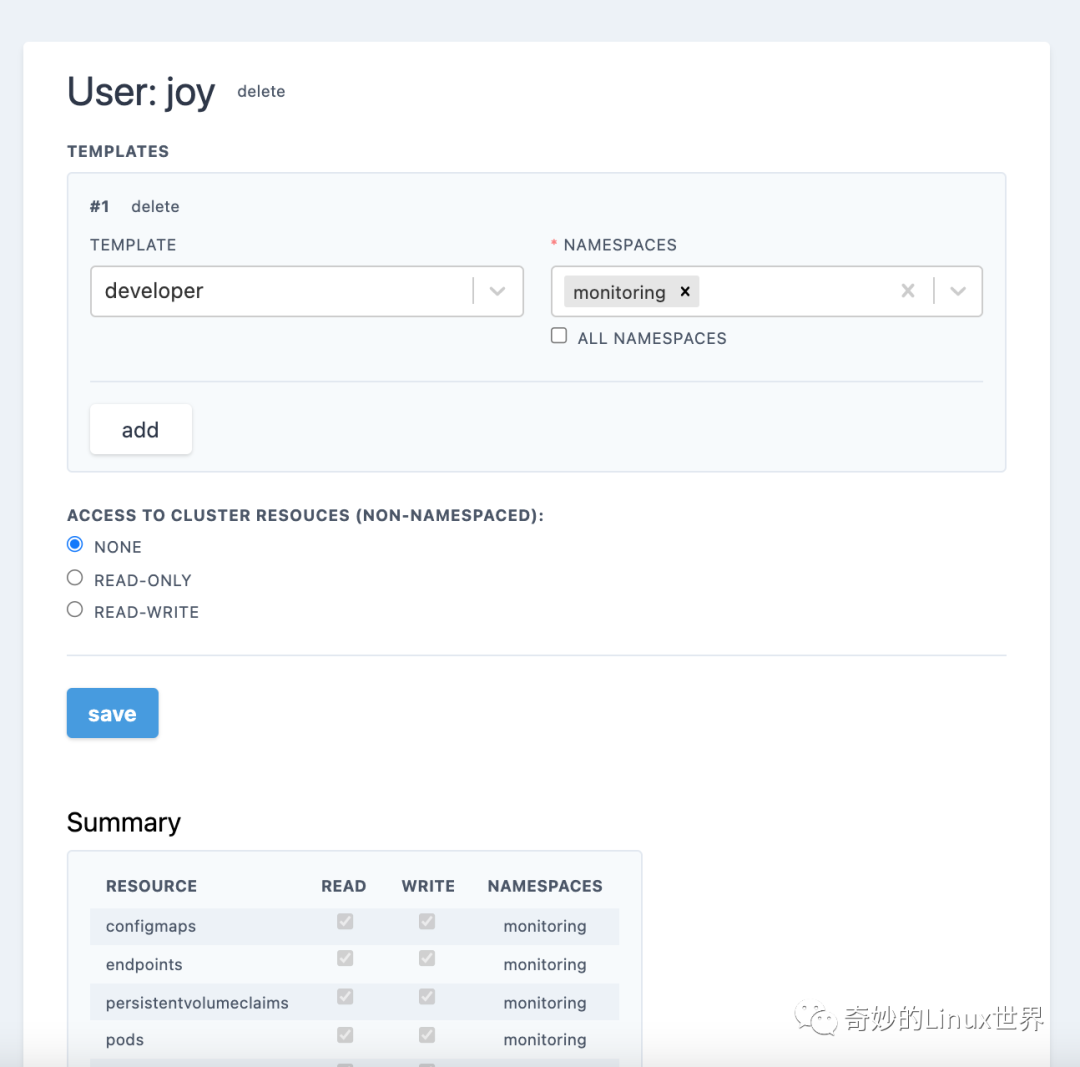
注意:这里可以使用预先定义的模版,模版的权限我们可以选中后在下方的 summay 或者选中模板时左侧的info 里查看。
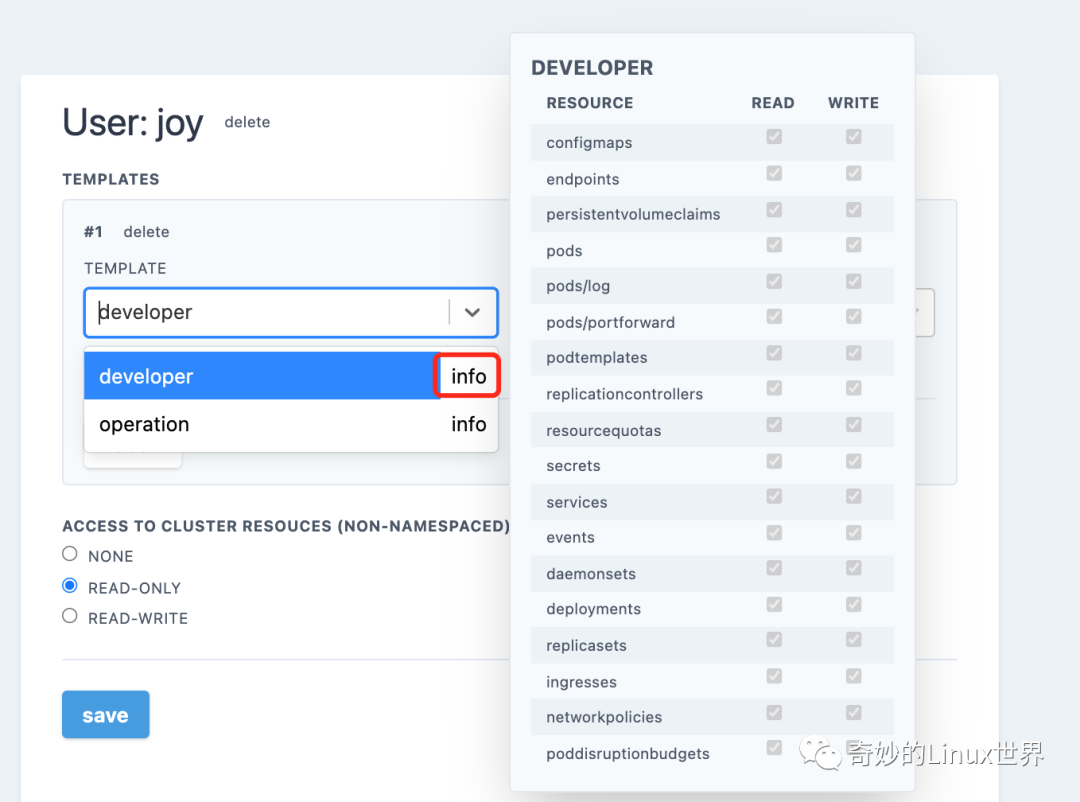
点击 save 后页面下方的 show kubeconfig for xxx 可以查看生成的 kubeconfig 我们可以复制其内容并保存为文件 joy-config。
验证
访问授权的
monitoring命名空间时,权限正常。
$ kubectl --kubeconfig joy-config -n monitoring get pod
NAME READY STATUS RESTARTS AGE
alertmanager-main-0 2/2 Running 0 6d23h
alertmanager-main-1 2/2 Running 0 6d23h
blackbox-exporter-7cc588b854-zbvhg 3/3 Running 0 22d
grafana-d99d69764-ck87h 1/1 Running 0 22d
kube-state-metrics-859b6bf99-9b94p 3/3 Running 0 22d
node-exporter-x4h2l 2/2 Running 0 191d
node-exporter-xxwkb 2/2 Running 0 23d
prometheus-adapter-7586ffcbdb-2zhzb 1/1 Running 0 22d
prometheus-alert-center-5655c9c95c-8jqx9 1/1 Running 0 22d
prometheus-k8s-0 2/2 Running 1 21d
prometheus-operator-69999459d6-s69xv 2/2 Running 0 22d
redis-exporter-6b694dfc97-rk5d2 1/1 Running 0 16d
redis-exporter-test-5795d6db56-2k886 1/1 Running 0 16d
ssl-exporter-6654bc6694-xvpmd 1/1 Running 0 22d
thanos-ruler-kubesphere-0 2/2 Running 0 21d
webhook-dingtalk-6769f4d79c-kmg4w 1/1 Running 0 22d访问未授权的其它命名空间时,显示如下报错。
$ kubectl --kubeconfig joy-config -n kube-system get pod
Error from server (Forbidden): pods is forbidden: User "system:serviceaccount:permission-manager:joy" cannot list resource "pods" in API group "" in the namespace "kube-system"自定义规则模板
默认只有 developer 和 operation 模板,模板都是以 template-namespaced-resources___ 为开头的 ClusterRole。例如:
template-namespaced-resources___
template-namespaced-resources___developer我们可以简单看一下我们的 k8s/k8s-seeds/seed.yml 文件中定义的模板
$ cat seed.yml
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: template-namespaced-resources___operation
rules:- apiGroups:- "*"resources:- "*"verbs:- "*"
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: template-namespaced-resources___developer
rules:- apiGroups:- "*"resources:- "configmaps"按照上面的格式,我们这里可以定义一个名为 test 的模板,只允许其查看 pod 的权限。
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:name: template-namespaced-resources___test
rules:- apiGroups:- "*"resources:- "pods"- "pods/log"- "pods/portforward"- "podtemplates"- "deployments"verbs:- "*"使用上面的 YAML 文件创建相应 ClusterRole 后,我们就可以在 Permission Manager 页面里使用这个模板了。
本文转载自:「 云原生实践者 」,原文:https://tinyurl.com/3brexmx7 ,版权归原作者所有。欢迎投稿,投稿邮箱: editor@hi-linux.com。


你可能还喜欢
点击下方图片即可阅读
万字长文详解 PaaS toB 场景下 Kubernetes 离线部署方案
点击上方图片,『美团|饿了么』大额外卖红包天天免费领

更多有趣的互联网新鲜事,关注「奇妙的互联网」视频号全了解!
